Understanding the Big Picture of Cybersecurity Starts with NIST
For any small and medium-sized business (SMB), the number of cybersecurity solutions to choose from can be overwhelming. If they are also not convinced cyberattacks pose a threat to them — as a recent CNBC survey shows — they may be even less inclined to consider taking action to improve their cybersecurity posture.
But SMBs that leave their assets vulnerable to exploitation face an existential threat. In 2020, for instance, 43% of cyberattacks targeted small businesses, according to a Verizon report.
Cue the managed service providers (MSP). When it comes to helping SMBs realize the acute risks inaction brings, MSPs have a crucial role to play. MSPs are ideally positioned to introduce the benefits of vulnerability management to their customers — and it’s especially helpful to frame the discussion in the context of the big picture of cybersecurity.
Aside from boosting your credibility by being able to function as a thought leader in cybersecurity, it helps your customer understand the full threat landscape.
So, how do you cut through the noise and secure buy-in from your SMB customers?
The answer: Lean on the NIST Cybersecurity Framework.
Let’s explain.
Guidelines no business can afford to ignore
Considered the gold standard for building an effective cybersecurity program, the framework provides the optimal context for an articulate conversation about cybersecurity risk.
Drafted by the National Institute of Standards and Technology (NIST) at the U.S. Department of Commerce, it’s designed to help businesses of all sizes better understand, manage, and reduce their cybersecurity risk and protect their networks and data. Although voluntary, no business that seeks to adopt best practices for cybersecurity protection can overlook the importance of this source.
Designed to improve communication about cybersecurity
Interestingly, one of the key aims of the NIST Cybersecurity Frameworks is to foster communication about risk and cybersecurity management amongst internal and external organizational stakeholders.
In response to a question on why organizations should use the framework, NIST replies:
“By providing a common language to address cybersecurity risk management, it is especially helpful in communicating inside and outside the organization. That includes improving communications, awareness, and understanding between and among IT, planning, and operating units, as well as senior executives of organizations. Organizations also can readily use the Framework to communicate current or desired cybersecurity posture between a buyer or supplier.”
A full understanding of the framework leaves an organization better equipped to prioritize investments and maximize the impact of each dollar spent on cybersecurity. In that regard, an MSP can use the framework to explain to customers how the cybersecurity protection and response process is categorized — and why it can make sense to focus on certain solutions over others.
Why it pays to focus on Identify and Protect
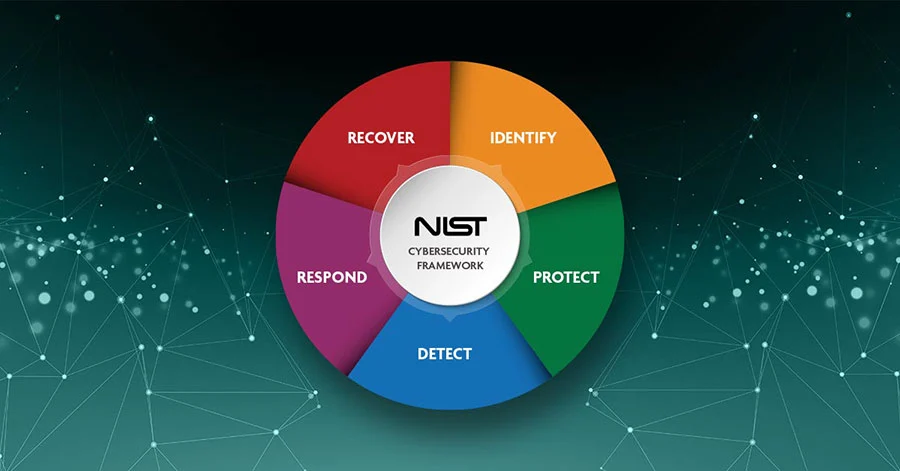
The backbone of the framework consists of five core functions around which all other elements are organized.
- Identify: Inventorying assets and vulnerabilities, measuring attack surface, prioritizing, baselining normal, threat modeling, risk assessment
- Protect: Preventing or limiting impact, patching, containing, isolating, hardening, managing access, vulnerability mitigation
- Detect: Discovering events, triggering on anomalies, hunting for intrusions, security analytics
- Respond: Acting on events, eradicating intrusion, assessing damage, forensic reconstruction
- Recover: Returning to normal operations, restoring services, documenting lessons learned, resiliency
In other words, the cybersecurity journey of any business starts with the “Identify” stage which establishes the foundation for future success in protecting an IT environment.
NIST states: “The Identify Function assists in developing an organizational understanding to managing cybersecurity risk to systems, people, assets, data, and capabilities. Understanding the business context, the resources that support critical functions, and the related cybersecurity risks enables an organization to focus and prioritize its efforts, consistent with its risk management strategy and business needs.”
In a sales conversation about vulnerability management, it then makes sense to emphasize that the first two functions — Identify and Protect — both serve to minimize vulnerabilities, unlike Detect, Respond, and Recover which define what the response to an attack looks like once it occurs.
This ties right into the concepts of “left of boom” and “right of boom,” which give MSPs the ability to effectively analyze security conflicts from both an offensive and defensive perspective. The former refers to the event sequence that occurs before an attack, while the latter addresses the events that follow. By focusing on Identify and Protect, MSP customers will minimize the "right of boom" impact and business losses that can result from cyberattacks.
‘You can’t protect what you don’t know’
As the saying goes, “You can’t protect what you don’t know.” Companies that lack visibility into all assets can neither protect their environment nor reduce their attack surface. By focusing on Identify and Protect, a business will reduce the number of episodes that require activation of the next three steps.
NIST defines Identify and Protect as follows:
The Identify Function
- assists in developing an organizational understanding of managing cybersecurity risk to systems, people, assets, data, and capabilities
- helps define the business context, the resources that support critical functions, and the related cybersecurity risks that enable an organization to focus and prioritize its efforts in alignment with its risk management strategy and business needs
The Protect Function
- outlines appropriate safeguards to ensure the delivery of critical infrastructure services
- supports the ability to limit or contain the impact of a potential cybersecurity event
Final word
All businesses, large and small, have much to gain from building cyber resilience and MSPs can play a leading part in helping them do so. By using the NIST Cybersecurity Framework to initiate an informed client discussion about the volatile threat landscape, MSPs can prove the importance of focusing on the first two functions: identify and protect. At the same time, they can turn vulnerability management into a new source of revenue growth.
ConnectSecure is here to help. Contact us today to learn more.
Read more:
What role does vulnerability management play in cyber insurance?
5 ways vulnerability testing can drive profits for MSPs
What MSPs should look for in a vulnerability management solution

