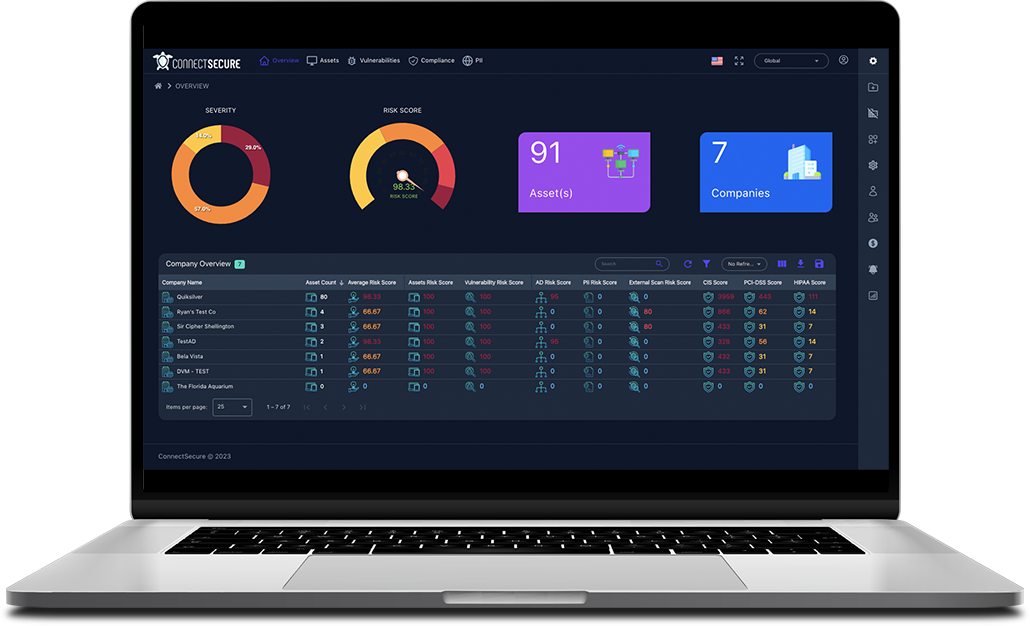

The all-in-one Vulnerability and Compliance Management Platform built for MSPs
Integrated solutions to elevate client security & compliance

Vulnerability Management
Continuously identify, prioritize, and remediate vulnerabilities across your clients’ environments to reduce risk and strengthen security posture.
Compliance Management
Simplify complex regulatory requirements with pre-built frameworks and automated assessments that help your clients achieve and maintain compliance.
Premium Features
Gain comprehensive visibility into cloud environments to identify misconfigurations, excessive permissions, and security gaps across major cloud providers.Build a complete security practice with ConnectSecure
Identify
Discover and assess your clients’ entire technology footprint:
Monitor
Continuously track security and compliance status:
Remediate
Address issues efficiently with guided workflows:
Report
Demonstrate your value with comprehensive reporting:
ConnectSecure is the only platform that includes these scans:
Internal Vulnerability Scans
Detect and identify system vulnerabilities across operating systems, applications, and networks to protect against potential exploits before they can be used by attackers.External Vulnerability Scans
Scan your client’s internet-facing assets including websites, APIs, networks, ports, and applications to identify vulnerabilities that may expose sensitive data to malicious actors.Application Baseline Scans
Create and monitor application configurations against secure baselines to quickly identify misconfigurations and deviations that could expose clients to risk.Attack Surface Scans
See your network through an attacker’s eyes to identify vulnerabilities across the entire IT ecosystem, providing 360-degree visibility of security gaps.Firewall Scans
Detect and analyze firewall configurations to identify misconfigured rules, weak access controls, and security gaps that could allow unauthorized network access.Active Directory Scans
Identify security gaps in Active Directory implementations including excessive permissions, weak password policies, and misconfigured security settings.Compliance Scans
Ensure clients meet essential cybersecurity benchmarks by aligning with frameworks like NIST, CIS, and PCI DSS, helping them maintain regulatory compliance.PII Scans
Safeguard personal information from cyber threats with comprehensive PII discovery that identifies sensitive data like names, credit card numbers, social security numbers, and addresses across all systems.M365 Scans
Identify security vulnerabilities in Microsoft 365 environments including excessive permissions, weak authentication settings, and configuration issues that put data at risk.Google Workspace Scans
Discover security misconfigurations in Google’s cloud productivity suite that could lead to data exposure, unauthorized access, and compliance violations.Web Application Scans
Identify security flaws in client-facing web applications without requiring direct control, focusing on misconfigurations and vulnerabilities attackers could exploit.
Transform security into a revenue driver
Deliver high-value vulnerability management and compliance services that create new revenue streams while strengthening client relationships.
- Expand your service offerings with ready-to-deploy compliance frameworks and assessments
- Increase monthly recurring revenue by adding security services your clients need
- Differentiate your MSP in a crowded market with comprehensive security capabilities

Maximize your resources with automation
Enjoy the impact of automating time-consuming security tasks so your team can focus on high-value activities while supporting more clients.
- Save valuable technician time with automated vulnerability scanning and patching workflows
- Streamline compliance work by leveraging 20+ built-in compliance frameworks
- Simplify reporting with white-labeled, detailed reports that prove your value to clients
- One agent handles all scanning needs—no deployment headaches

Reduce risk across your client base
Take a proactive approach to security by identifying vulnerabilities before they become problems.
- Continuous vulnerability monitoring with access to 230,000+ CVEs that are constantly updated against the US government’s National Vulnerability Database
- Comprehensive protection against both internal and external vulnerabilities
- Comprehensive attack surface visibility across assets, applications, and networks
- EPSS prioritization helps focus remediation efforts on the most critical vulnerabilities first
- Integrated with your PSA for seamless service ticket management

AI-powered reporting that proves your impact
Generate executive-ready and technical reports in minutes. ConnectSecure’s AI-driven reporting suite turns complex security data into clear insights, helping you demonstrate results, guide remediation, and strengthen client trust.
- 360 Assessment Report for executive-level insights on strengths, weaknesses, and next steps
- Company Health Report summarizing performance across all managed companies
- Technical Report (Cybernotes) with actionable items for remediation teams
- Customizable templates to add, remove, and reorder report sections
- GPT-generated analysis available in multiple languages, included in the standard tier

Meet cyber insurance requirements
Help clients navigate the increasingly complex cyber insurance landscape while demonstrating your value as a security partner.
- Satisfy insurance prerequisites with comprehensive vulnerability scanning and management
- Document remediation efforts with detailed audit trails and reporting
- Demonstrate compliance with various frameworks required by insurers
- Reduce premiums by implementing and documenting security best practices

Join our community-led approach
We’re the only community-led vulnerability and compliance management platform built specifically for MSPs and MSSPs.
- Weekly partner calls keep us connected to your evolving needs
- Product roadmap influenced by partners like you
- Ongoing education and resources to help grow your security practice
- Dedicated partner success team supporting you every step of the way
Want to see ConnectSecure in action?
What our Partners are saying

ConnectSecure
Great Tool for a Great Price
ConnectSecure
Essential Security Tool for SMB
Does What We Need
Right Choice for VA Management
Great Tool
Daily Vulnerability Scans
Good Stuff
Great Product for the Price
Product Comparison
| ConnectSecure | RapidFire Tools | Qualys | Tenable | |
|---|---|---|---|---|
| Asset Discovery and Scanning | ||||
| Automated SSL Checks (Ciphers and Protocols) | ||||
| Azure Active Directory Users and Groups Compliance | X | X | ||
| External Scans | ||||
| Intune | X | X | X | |
| Local Active Directory Users and Groups Compliance | X | X | ||
| Office 365 Assets and Secure Score | X | X | ||
| Port Scans | ||||
| SMB/CIFS Shares | X | X | ||
| Software Inventory | X | |||
| Application Baseline Scan | ||||
| Web Vulnerability Scanner | X | |||
| PII Scan | ||||
| EPSS Scoring | X | |||
| Supported Operating Systems | ||||
| Linux (Ubuntu/Redhat/CentOS/AmazonLinux) | ||||
| Mac OS | ||||
| Windows Vulnerabilities | ||||
| Dashboards and Reporting | ||||
| Automated Monthly Review Presentation | X | X | X | |
| Build Your Own Report | X | |||
| Centralized Dashboard | ||||
| Predefined Reports | ||||
| Remediation | ||||
| Software Patches and Updates Check | ||||
| Architecture and Infrastructure | ||||
| Unified Agent | X | X | ||
| User and Role Based Access Control | X | X | X | |
| Flexibility | ||||
| Configurable Notifications | X | |||
| Configurable Schedulers | X | |||
| Single License covers all Assets | X | |||
| Subnet Scan | ||||
| Extensibility | ||||
| Lightweight agent to run with RMM tools | X | |||
| Rest API | X | |||
| Webhooks support | X | X | X | |
| Compliance | ||||
| Compliance Scans (NIST, CIS, GDPR, PCI DSS, HIPAA, Cyber Essentials, Essential Eight) | X | X | X | |
| Compliance Assessments | X | X | X | |
No CVE












