

Focus on the ConnectSecure functions that are most important to your MSP
ConnectSecure’s 90-minute Product Sessions dive deep into a specific function of the ConnectSecure Platform, MSPs unlock new value, streamline service delivery, and strengthen client outcomes. From configuring application baselines and deploying agents to scanning cloud environments and managing attack surfaces, these expert-led sessions offer hands-on guidance and actionable insights. Whether you’re looking to optimize your onboarding process, enhance threat detection, or support compliance, these focused trainings are designed to elevate your practice—one powerful capability at a time.
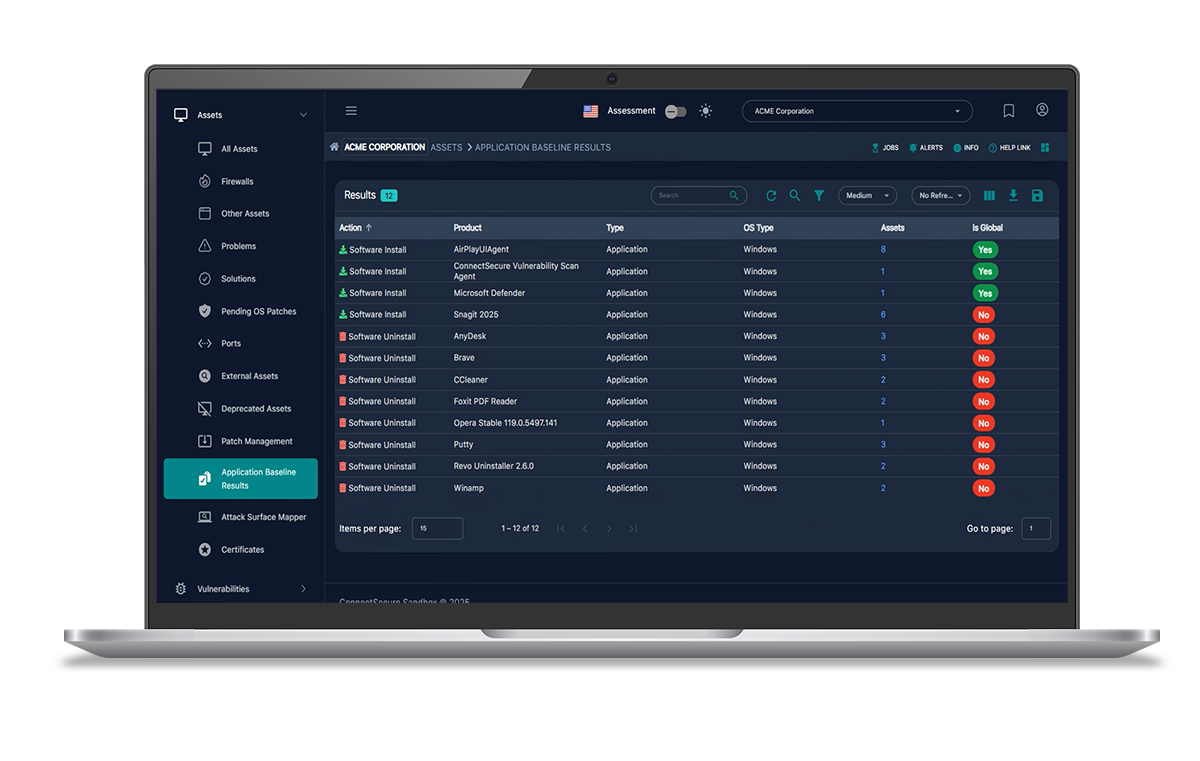
Application Baseline
Work with a ConnectSecure expert to define and configure your application baseline. Track known-good software across endpoints to detect drift, unauthorized tools, or shadow IT.
- Establish a clean, approved software inventory across environments
- Detect unauthorized or high-risk applications quickly
- Reduce software sprawl and enforce policy controls
- Support frameworks that require software allow-listing
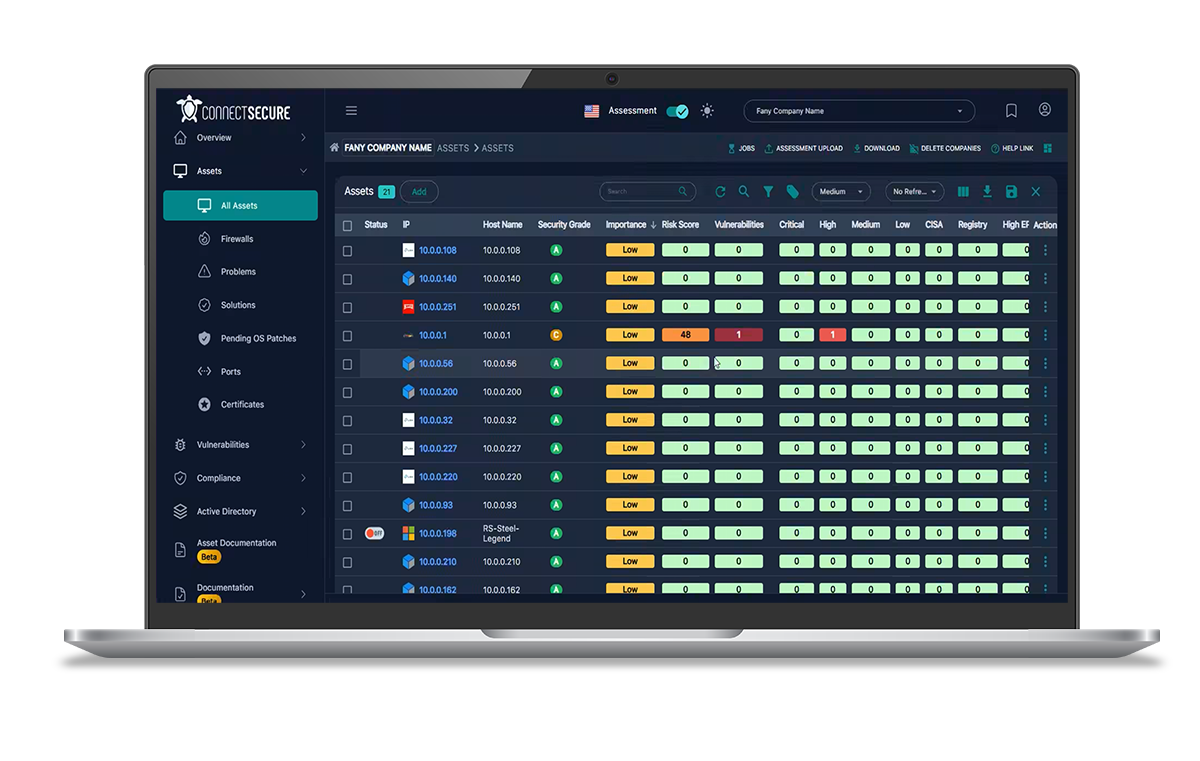
Assessment/Prospect Scanning
Use this session to configure and execute an assessment scan—ideal for onboarding new clients, validating security posture, or conducting risk reviews.
- Quickly surface risks in a new or unmanaged environment
- Generate branded reports to support pre-sales or QBRs
- Uncover remediation and upsell opportunities early
- Establish a repeatable scan method for future prospects
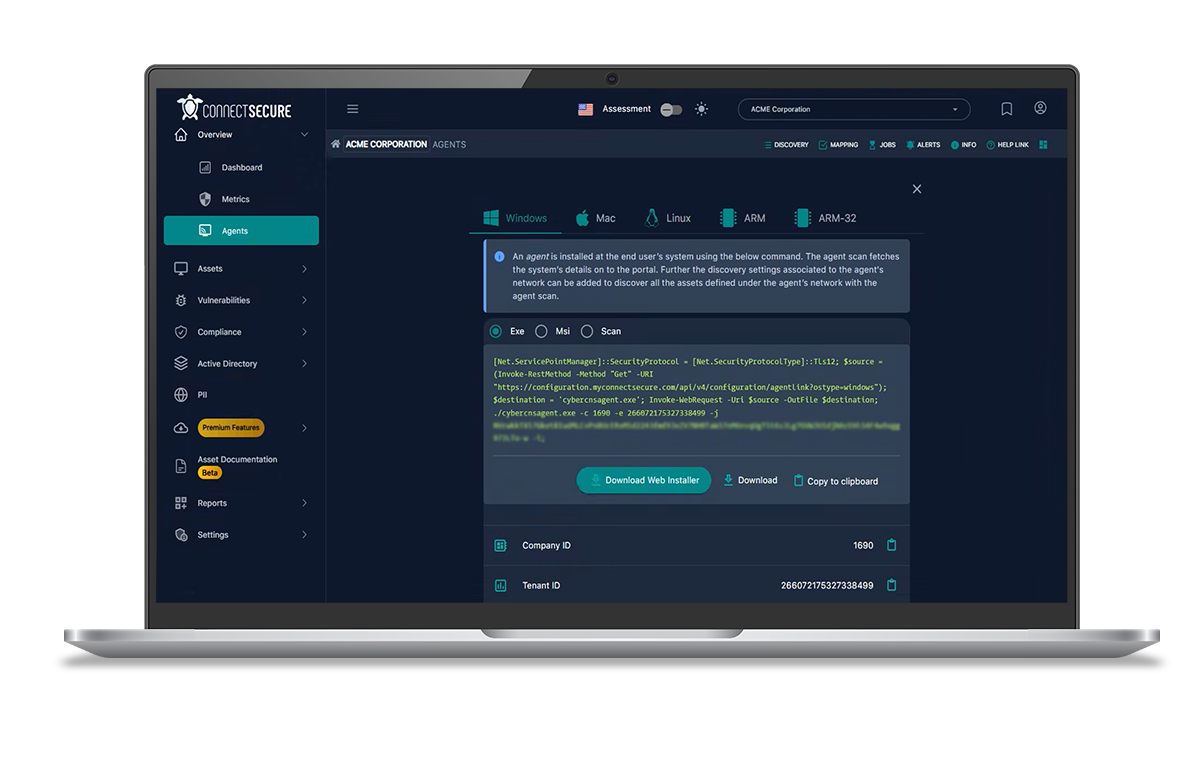
Agent Deployment Methods
Review and implement agent deployment strategies—RMM, API, scripting, or manual—tailored to your environment and preferred automation tools.
- Select the right method for each client scenario
- Automate mass deployment to speed up onboarding
- Ensure agent consistency across diverse infrastructure
- Reduce manual effort and deployment errors
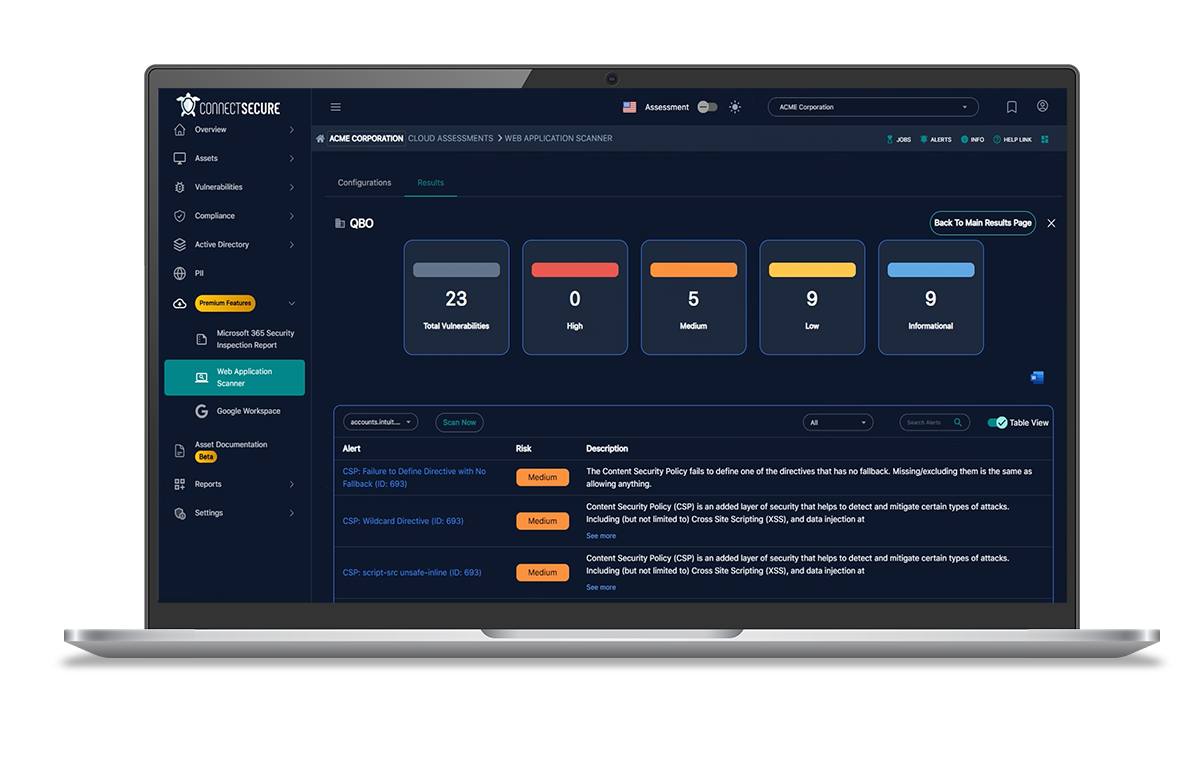
Cloud/Web Application Scanning
Configure and execute scans for cloud infrastructure and public-facing web applications. Identify weaknesses in IaaS, SaaS, and web platforms using ConnectSecure tools.
- Discover vulnerabilities in AWS, Azure, or other cloud platforms
- Scan web apps for OWASP Top 10 risks and common exploits
- Identify misconfigurations in public-facing assets
- Ensure compliance with external-facing system policies
Event Set/Integration Profile/Alerting
Design and configure event sets, alerting rules, and integrations with tools like Slack, email, and PSA systems to drive automated response and visibility.
- Route critical alerts to the right teams or systems
- Reduce noise by tuning thresholds and alert conditions
- Speed up response time with contextual alerts
- Close the loop with direct PSA or helpdesk integration
External/Attack Surface Management
Set up external scanning and attack surface discovery. Identify exposed services, shadow IT, and open vulnerabilities on public-facing assets.
- Continuously monitor internet-exposed assets
- Uncover forgotten or misconfigured public services
- Prioritize external risks with the highest business impact
- Validate attack surface reduction efforts over time
Internal/Network Scanning
Implement internal network scanning to evaluate risks inside the perimeter. Identify lateral movement paths, missing patches, and unmonitored assets.
- Discover unmanaged or rogue devices on internal networks
- Scan internal assets for outdated or vulnerable software
- Strengthen segmentation and internal control visibility
- Reduce risk of lateral movement and privilege escalation
PII Scanning
Enable and configure PII discovery across endpoints and file shares. Understand where sensitive data lives and whether it’s properly protected.
- Locate personally identifiable information across systems
- Support data privacy and compliance obligations (e.g., GDPR, CCPA)
- Identify storage or transmission of PII in risky locations
- Provide documentation of controls for audits and reviews