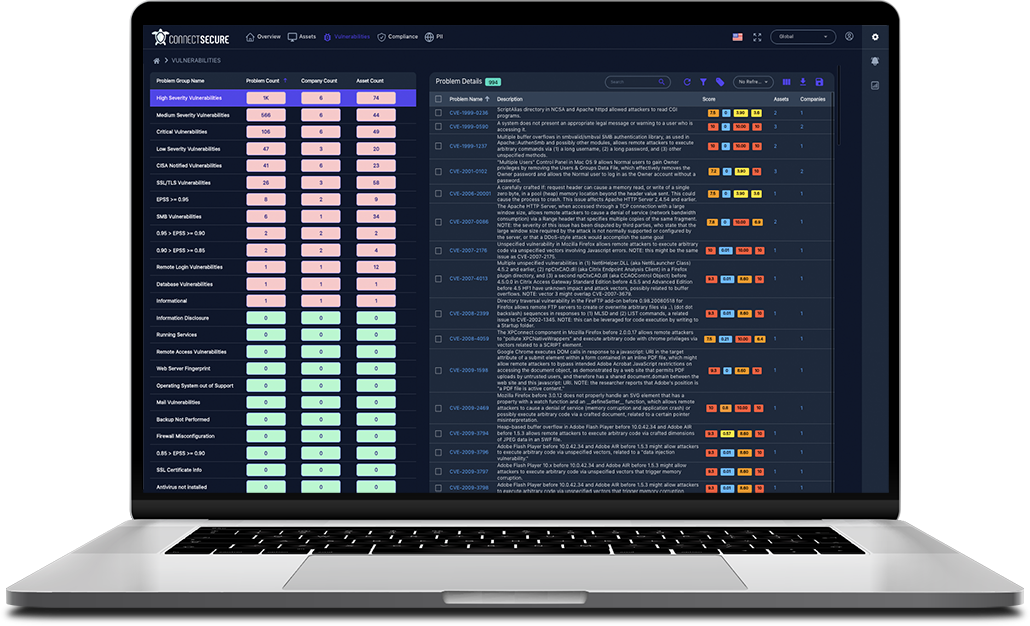

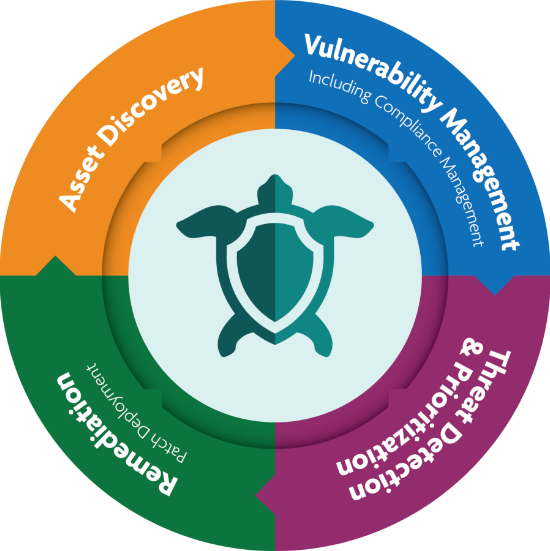
Complete vulnerability lifecycle management for MSPs
ConnectSecure delivers true end-to-end vulnerability management—including risk assessments and continuous scanning—through asset discovery, vulnerability detection, risk-based prioritization, and guided remediation workflows designed specifically for MSP and their clients.
The only platform that includes these scans:
- Internal Vulnerability Scans
- External Vulnerability Scans
- Application Baseline Scans
- Attack Surface Scans
- Active Directory Scans
- Compliance Scans
- PII Scans
- Firewall Scans
- M365 Scans
- Google Workspace Scans
- Web Application Scans
Our end-to-end approach follows a complete process

Real-time threat intelligence in action
While most solutions scan periodically, ConnectSecure maintains live connections with the NIST National Vulnerability Database (NVD) and Common Vulnerabilities and Exposures (CVE) repositories, syncing multiple times daily to track over 230,000 known vulnerabilities.
When new threats emerge:
- Our engine immediately maps threats to your client assets
- EPSS scoring analyzes exploitation probability—not just theoretical severity
- Automated workflows create prioritized remediation tickets
- Integration with PSA platforms streamlines technician assignment
- Patch verification confirms successful remediations
This continuous cycle runs 24/7, creating a proactive defense against evolving threats without overwhelming your technical team.

Scan both internal networks and external attack surface
Complete Asset Discovery & Inventory
- Uncover the Full Attack Surface: Automatically detect and catalog every device, application, and potential entry point across client networks—even previously unknown assets
- Cloud Service Detection: Identify shadow IT and authorized cloud applications across client environments with 99.8% accuracy
- Service and Application Fingerprinting: Map installed software, versions, and configurations to enable precision vulnerability targeting
Multi-Vector Vulnerability Detection
- External Perimeter Scanning: Hunt for exposed ports, misconfigured services, and exploitable entry points from an attacker’s perspective
- Internal Network Assessment: Deep-scan internal networks with agent and agentless options for maximum coverage
- PII Exposure Detection: Locate unprotected personally identifiable information with machine learning pattern recognition

Stop chasing false positives with smart prioritization
EPSS: Exploitation Prediction Scoring System
ConnectSecure is the only MSP-centric solution leveraging EPSS—analyzing actual exploitation data to predict which vulnerabilities pose the greatest real-world risk.
- Saves significant time compared to traditional CVSS-only prioritization
- Prioritizes vulnerabilities with proven exploitation histories
- Adjusts risk profiles based on threat intelligence
- Maps dependencies between vulnerabilities for attack chain analysis

Fix faster with automated remediation
ConnectSecure streamlines the remediation process with integrated workflows and automated patching capabilities:
Efficient Remediation
- Application Patching: Install security patches for over 600 third-party software titles to ensure comprehensive protection against vulnerabilities in third-party software
- Automated Scheduling: Set automatic schedules or policies to ensure applications are always current without manual intervention
- CVE Intelligence: View Common Vulnerabilities and Exposures (CVEs) linked to missing application patches for an informed security approach
- Direct Fix Links: Receive recommended fix/KB links for each patch, ensuring prompt remediation

Turn technical data into clear client reports
ConnectSecure’s specialized reporting capabilities convert complex vulnerability data into actionable insights:
Comprehensive Reporting
- Dashboard Views: At-a-glance visualization of vulnerability status across all clients
- Role-Based Reports: Tailored for different stakeholders—from technical teams to executives
- White-Label Reports: Professionally branded reporting under your company identity
- Compliance Mapping: Automatic correlation between vulnerabilities and regulatory frameworks

“Switching to ConnectSecure was a breath of fresh air. The platform’s stability, ease of use, and responsive support team are all big wins for us.”
Trent Gasser
IT Consultant, Palitto Consulting
Download the case study to get the whole story.
Real results straight from our MSP community

Mitchell Matter
Co-founder | LockIT Technologies
Trent Gasser
IT Consultant | Palitto Consulting Services
Luis Alvarez
CEO | Alvarez Technology Group
Simon Hopkin
Head of Cyber Security | ITPStool for us to drive engagement. It’s very quick and easy to deploy and you get almost immediate results.”

Christophe Gagnon
Director | CyberVision 24/7
Karl Bickmore
CEO | Tech IT
Dennis Houseknecht
CTO | WatSec Cyber Risk Management