The Stats MSPs Need to Show SMBs Are Not Immune to Cyber Threats
Although high-profile cyber attacks have put cybersecurity on the radar of small and midsize businesses (SMBs), many are not fully aware of the extent of the threats they actually face; nor do they have the in-house resources to take effective action.
Far from guarding a single entry point, SMBs need to understand the scope of the attack surface in order to secure their assets. As a managed service provider (MSP), you’re uniquely positioned to provide that knowledge.
Amid growing cyber risk awareness and pressure to comply with cyber insurance requirements, Paul Rouse, president and owner of Rouse Consulting Group, a leading MSP in Illinois, has found his SMB customers are searching for support. By introducing continuous scanning, proactive vulnerability assessment, and support for critical compliance requirements, RCG has successfully met both current customer needs and won new business. (Read the full story here)
Stats Prove SMBs Are Vulnerable to Attack
Unlike enterprise organizations that dedicate entire teams to cybersecurity, small business leaders typically wear many hats, making cybersecurity one priority among many. Despite what they may think, this dynamic leaves them particularly vulnerable to threat actors — and the stats prove it.
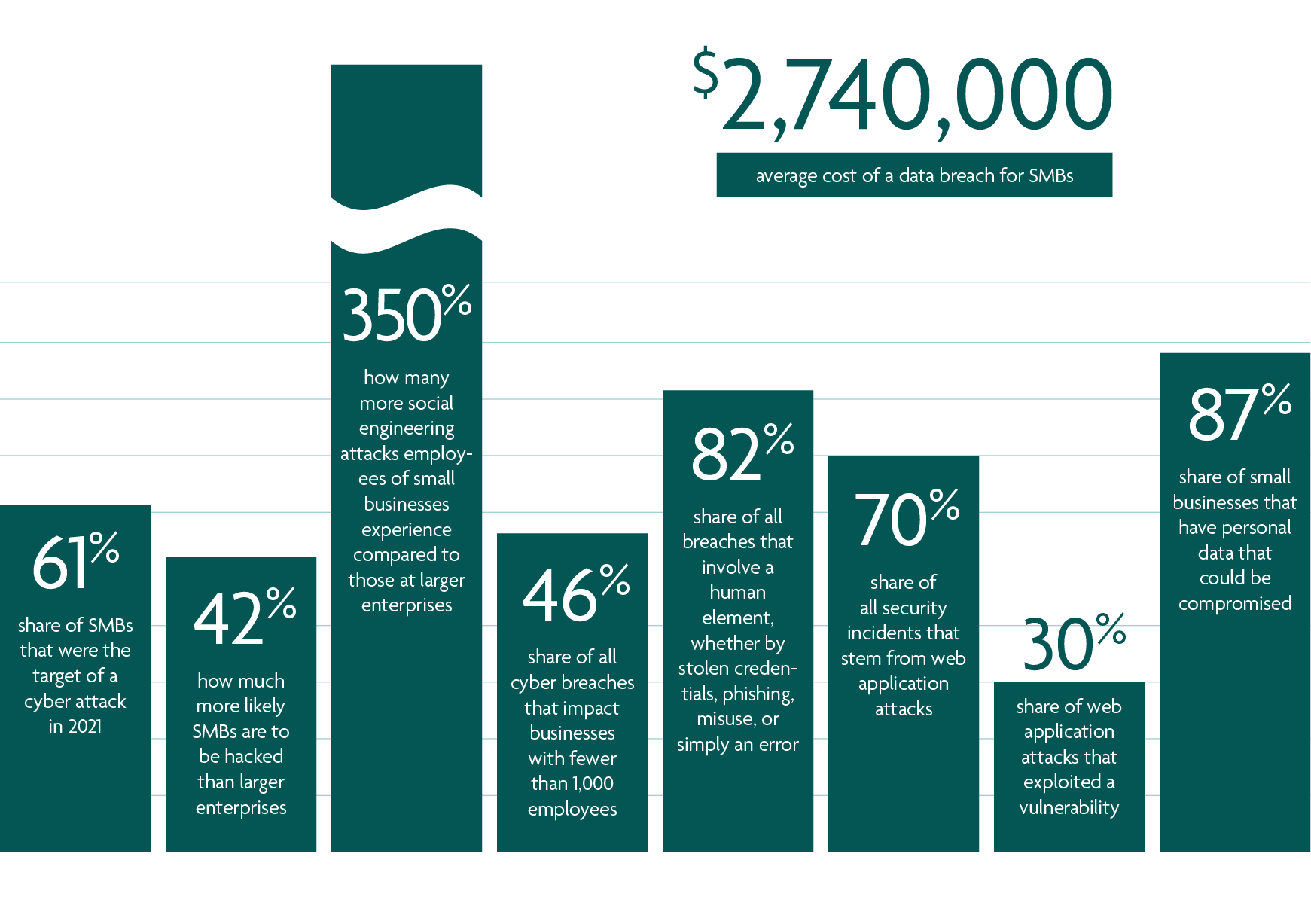
- 61% — share of SMBs that were the target of a cyber attack in 2021 (2022 Data Breach Investigations Report by Verizon)
- 42% — how much more likely SMBs are to be hacked than larger enterprises (National Cyber Security Alliance)
- 350% — how many more social engineering attacks employees of small businesses experience compared to those at larger enterprises (Barracuda Research)
- 46% — share of all cyber breaches that impact businesses with fewer than 1,000 employees (Verizon)
- 82% — share of all breaches that involve a human element, whether by stolen credentials, phishing, misuse, or simply an error (Verizon)
- 70% — share of all security incidents that stem from web application attacks (Verizon)
- 30% — share of web application attacks that exploited a vulnerability (Verizon)
- 87% — share of small businesses that have personal data that could be compromised (Digital.com survey)
- $2.74 million — average cost of a data breach for SMBs (IBM Cost of a Data Breach Report 2022)
These stats are especially notable in light of the findings of a recent Digital.com survey of 1,250 businesses with fewer than 500 employees:
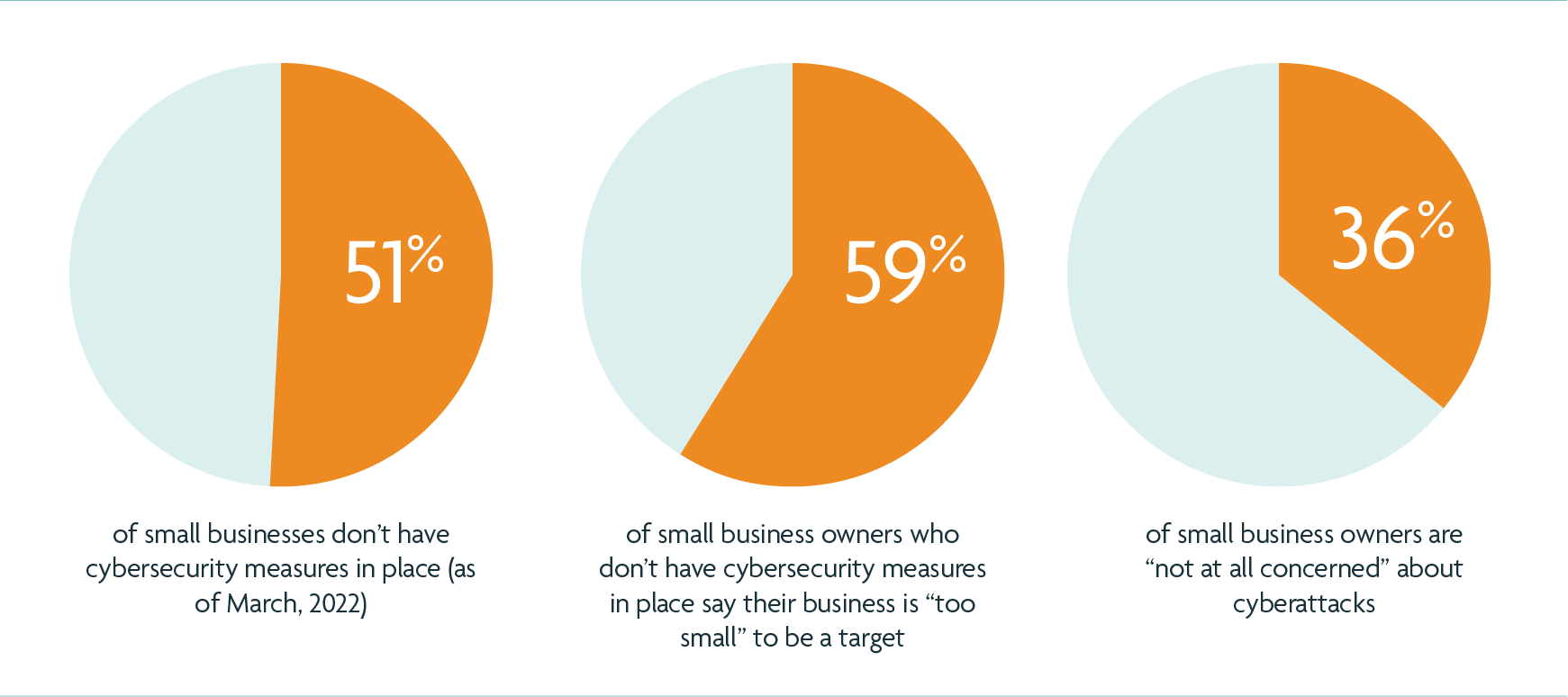
- 51% of small businesses don’t have cybersecurity measures in place (as of March, 2022)
- 59% of small business owners who don’t have cybersecurity measures in place say their business is “too small” to be a target
- 36% of small business owners are “not at all concerned” about cyberattacks
Looming Threat Cannot Be Ignored
Cybersecurity experts go as far as telling BBC the lack of preparedness among U.S. small businesses is the “Achilles heel” of the American economy. Aside from the potential devastating impact of a cyber attack on the business itself, ranging from legal fees and regulatory filings to steep fines and reputation damage, it can reverberate throughout the supply chain, hitting larger companies as well. In fact, cybercriminals target SMBs as an entry point to breach the larger corporations, increasing the threats SMBs face.
The rise of remote work has further complicated the task for resource-stretched SMBs by expanding the attack surface well beyond office networks. Regardless of company size, threat actors typically leverage four key paths to access the estate: credentials, phishing, botnets, and vulnerability exploitation. In the words of the 2022 Verizon data breach report, “no organization is safe without a plan to handle them all”:
Credentials
Credential-based attacks is a common method that often involves stealing or guessing a legitimate user's login credentials (username and password). Once the attacker has these credentials, they can bypass security measures and access sensitive data, manipulate systems, or even deploy malware. Credential stuffing, phishing, keylogging, man-in-the-middle attacks, and brute force are all examples of this type of attack.
Phishing
Phishing attacks are a common and persistent threat due to their simplicity and effectiveness. The main purpose is to trick the recipient into believing that the message is something they want or need, like a request from their bank or a note from a colleague, and to click a link or download an attachment.
Botnets
A botnet is a collection of internet-connected devices, which may include computers, servers, mobile devices and internet of things devices that are infected and controlled by a common type of malware. The devices are compromised and controlled by a remote attacker, often without the knowledge of their owners. This network of hijacked devices is used by attackers to perform coordinated tasks simultaneously. The significance and danger of botnets lie in their ability to leverage the collective power of numerous devices, enabling them to carry out large-scale attacks that would not be possible with a single device.
Vulnerability exploitation
According to the most recent Verizon figures, vulnerability exploitation now makes up 7% of all security breaches, a doubling over the previous year. Between 2020 and 2021, the proportion of vulnerability exploits in web application attacks also grew 10 times.
For instance, a hacker might use a vulnerability in a web application to inject malicious code (SQL injection), allowing them to access, modify, or delete data in the application's database. Alternatively, they might exploit a buffer overflow vulnerability in an operating system or an application, causing the system to crash or allowing the attacker to execute their own code.
Attackers use what Verizon calls “an opportunistic attack sales funnel.” They first scan for IPs and open ports, then they move on to crawling for specific services and testing for specific Common Vulnerabilities and Exposures (CVE), before finally trying Remote Code Execution (RCE) to gain access to the system.
The Way Forward
MSPs can help their SMB clients build cyber resilience amid escalating and increasingly sophisticated cyber attacks. Whether they remain in the dark about the threat level or lack the expertise and bandwidth to implement a cybersecurity strategy, you have an opportunity to position your business as a partner to lean on in a volatile time. With a cybersecurity platform featuring everything you need to identify and prioritize high-risk vulnerabilities for remediation, you can win more business and deliver enhanced service to your current clients. We can show you how.
Contact ConnectSecure today or get started right away with a 14-day free trial.
Read more:
The economic case for ConnectSecure’s vulnerability remediation
5 ways vulnerability testing can drive profits for MSPs
Biden’s cybersecurity strategy: Will MSPs have to take responsibility?

