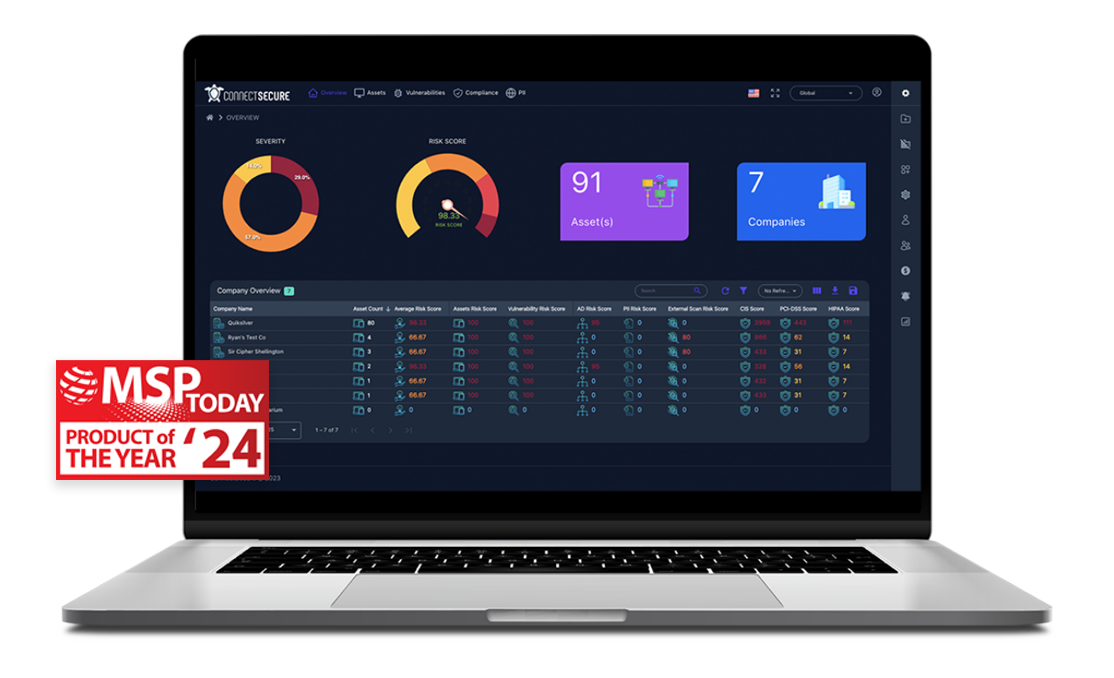
The All-in-One Vulnerability & Compliance Platform Built for MSPs
Win more deals with risk assessments. Scale your compliance services. Automate vulnerability management.
Take a 14-day free trial of ConnectSecure Premium Edition.
ConnectSecure’s MSP-tailored platform transforms your most common cybersecurity risk and compliance policy challenges into revenue opportunities. Charge up your security practice with:
- Automated vulnerability remediation: Go beyond just finding vulnerabilities — automatically patch third-party applications your RMM might miss
- Always-on attack surface monitoring: Continuously scan external, WAN, and LAN environments to protect clients from emerging threats
- Compliance and audit readiness: Provide detailed IT asset hygiene reports required by compliance frameworks and auditors
- Complete IT asset discovery: Know every device and application in your clients' networks
- Risk-based prospecting tools: Prove your value and earn trust by showing prospects their actual security gaps
- Deep cloud visibility: Leverage Google Workspace and M365 assessments as well as Web Application Scanning to identify misconfigurations and more (all included in Premium)
Start Your Free 14-Day Trial of ConnectSecure Premium Edition. No credit card required.
Bonus: We favor pay-as-you-go over long-term contracts.
Everything Your MSP Needs to Deliver Enterprise-Grade Protection
Real results straight from our MSP community

Mitchell Matter
Co-founder | LockIT Technologies
“Implementing ConnectSecure has significantly improved our approach to cybersecurity. The efficiency gained from agent-based scanning and the cost savings have allowed us to offer top-tier protection to our clients without breaking the bank.”

Trent Gasser
IT Consultant | Palitto Consulting Services
“The platform is intuitive and user-friendly, and our team readily adopted it. It’s become a talking point in most new client conversations and strategy meetings with existing customers.”

Luis Alvarez
CEO | Alvarez Technology Group
“ConnectSecure allows us to run regular, in-depth vulnerability scans, ensuring our patching strategies are effective and any new security weaknesses are quickly identified and addressed.”

Simon Hopkin
Head of Cyber Security | ITPS
“ConnectSecure has been an excellent
tool for us to drive engagement. It’s very quick and easy to deploy and you get almost immediate results.”
tool for us to drive engagement. It’s very quick and easy to deploy and you get almost immediate results.”

Christophe Gagnon
Director | CyberVision 24/7
“We use everything—external scanning, reports, PII detection, firewall integration… The value for the price is really good.”

Karl Bickmore
CEO | Tech IT
“We’re providing better reporting, better data, better planning, and it’s helping us win more deals—like significantly more deals—and our sophistication has gone way up.”

Dennis Houseknecht
CTO | WatSec Cyber Risk Management
“There’s no all-in-one tool on the market—and I follow the market pretty closely—that has the depth and breadth of ConnectSecure’s vulnerability scans, and that’s presented in such an actionable way.”

Tim Fournet
CISO | Rader
“The fact this platform is built with service providers in mind means we can use it across our client base hassle-free at a cost that makes it a no-brainer to bundle with our other services.