The all-in-one platform for controlling risk and driving growth.
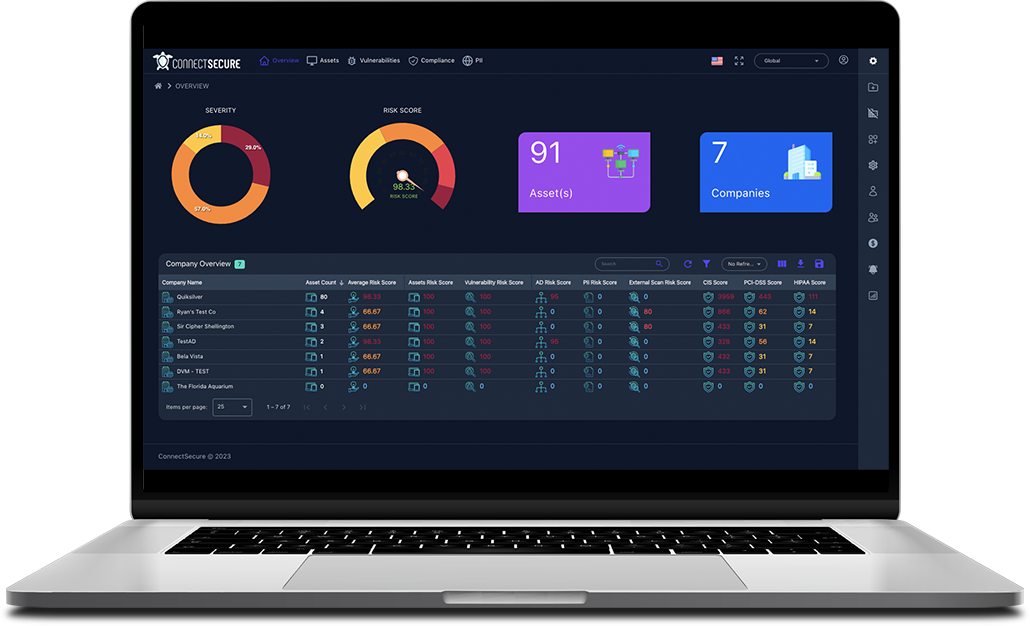
ConnectSecure is the MSP-centric platform that solves tool fatigue while helping you protect clients, meet compliance requirements, and grow your security practice—all with one affordable solution.
Must have for MSP!
“ConnectSecure has been our significant partner in assisting us to provide excellent service for our clients. Starting with the pricing to their support, ConnectSecure checks all the boxes. What impresses me the most is how they interact with their partners. If you want an all-in-one compliance/asset management/cybersecurity application, I highly recommend ConnectSecure!”

14-Day Free Trial. No Credit Card Required.
Trusted by thousands of MSPs.













Build a complete security practice with ConnectSecure
Identify
Discover and assess your clients’ entire technology footprint:
Monitor
Continuously track security and compliance status:
Remediate
Address issues efficiently with guided workflows:
Report
Demonstrate your value with comprehensive reporting:
Sign up for a 14-day free trial
Real results straight from our MSP community

Mitchell Matter
Co-founder | LockIT Technologies
Trent Gasser
IT Consultant | Palitto Consulting Services
Luis Alvarez
CEO | Alvarez Technology Group
Simon Hopkin
Head of Cyber Security | ITPStool for us to drive engagement. It’s very quick and easy to deploy and you get almost immediate results.”

Christophe Gagnon
Director | CyberVision 24/7
Karl Bickmore
CEO | Tech IT
Dennis Houseknecht
CTO | WatSec Cyber Risk Management
Tim Fournet
CISO | RaderConnectSecure is the only platform that includes these scans:
Internal Vulnerability Scans
Detect and identify system vulnerabilities across operating systems, applications, and networks to protect against potential exploits before they can be used by attackers.External Vulnerability Scans
Scan your client’s internet-facing assets including websites, APIs, networks, ports, and applications to identify vulnerabilities that may expose sensitive data to malicious actors.Application Baseline Scans
Create and monitor application configurations against secure baselines to quickly identify misconfigurations and deviations that could expose clients to risk.Attack Surface Scans
See your network through an attacker’s eyes to identify vulnerabilities across the entire IT ecosystem, providing 360-degree visibility of security gaps.Firewall Scans
Detect and analyze firewall configurations to identify misconfigured rules, weak access controls, and security gaps that could allow unauthorized network access.Active Directory Scans
Identify security gaps in Active Directory implementations including excessive permissions, weak password policies, and misconfigured security settings.Compliance Scans
Ensure clients meet essential cybersecurity benchmarks by aligning with frameworks like NIST, CIS, and PCI DSS, helping them maintain regulatory compliance.PII Scans
Safeguard personal information from cyber threats with comprehensive PII discovery that identifies sensitive data like names, credit card numbers, social security numbers, and addresses across all systems.M365 Scans
Identify security vulnerabilities in Microsoft 365 environments including excessive permissions, weak authentication settings, and configuration issues that put data at risk.Google Workspace Scans
Discover security misconfigurations in Google’s cloud productivity suite that could lead to data exposure, unauthorized access, and compliance violations.Web Application Scans
Identify security flaws in client-facing web applications without requiring direct control, focusing on misconfigurations and vulnerabilities attackers could exploit.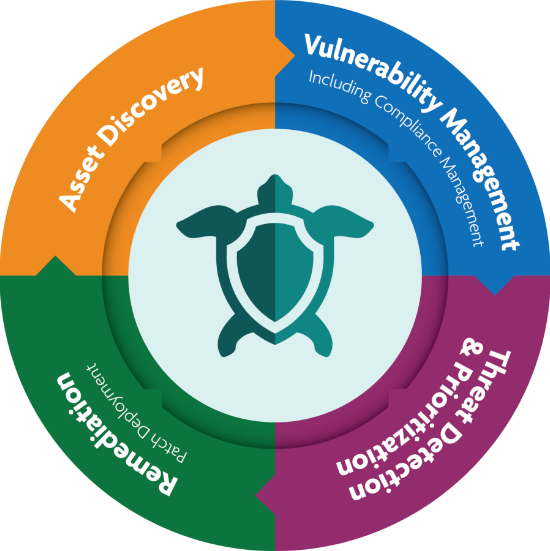
Complete vulnerability lifecycle management for MSPs
14-Day Free Trial. No Credit Card Required.
What our Partners are saying

ConnectSecure
Great Tool for a Great Price
ConnectSecure
Essential Security Tool for SMB
Does What We Need
Right Choice for VA Management
Great Tool
Daily Vulnerability Scans
Good Stuff
Great Product for the Price
Product Comparison
| ConnectSecure | RapidFire Tools | Qualys | Tenable | |
|---|---|---|---|---|
| Asset Discovery and Scanning | ||||
| Automated SSL Checks (Ciphers and Protocols) | ||||
| Azure Active Directory Users and Groups Compliance | X | X | ||
| External Scans | ||||
| Intune | X | X | X | |
| Local Active Directory Users and Groups Compliance | X | X | ||
| Office 365 Assets and Secure Score | X | X | ||
| Port Scans | ||||
| SMB/CIFS Shares | X | X | ||
| Software Inventory | X | |||
| Application Baseline Scan | ||||
| Web Vulnerability Scanner | X | |||
| PII Scan | ||||
| EPSS Scoring | X | |||
| Supported Operating Systems | ||||
| Linux (Ubuntu/Redhat/CentOS/AmazonLinux) | ||||
| Mac OS | ||||
| Windows Vulnerabilities | ||||
| Dashboards and Reporting | ||||
| Automated Monthly Review Presentation | X | X | X | |
| Build Your Own Report | X | |||
| Centralized Dashboard | ||||
| Predefined Reports | ||||
| Remediation | ||||
| Software Patches and Updates Check | ||||
| Architecture and Infrastructure | ||||
| Unified Agent | X | X | ||
| User and Role Based Access Control | X | X | X | |
| Flexibility | ||||
| Configurable Notifications | X | |||
| Configurable Schedulers | X | |||
| Single License covers all Assets | X | |||
| Subnet Scan | ||||
| Extensibility | ||||
| Lightweight agent to run with RMM tools | X | |||
| Rest API | X | |||
| Webhooks support | X | X | X | |
| Compliance | ||||
| Compliance Scans (NIST, CIS, GDPR, PCI DSS, HIPAA, Cyber Essentials, Essential Eight) | X | X | X | |
| Compliance Assessments | X | X | X | |
No CVE
Sign up for a 14-day free trial
Frequently Asked Questions about ConnectSecure
Positioning
Is ConnectSecure Vulnerability Management (CS-VM) an agent, a probe, or something else?
Can CS-VM scan nodes associated with employees that Work from Home?
What are the kinds of assets that CS-VM can scan? (routers, firewalls, PCs, etc.?)
I have an RMM and antivirus software, why do I need CS-VM?
CS-VM is promoted as being an all-in-one solution. What exactly is included that competitive products might distribute across multiple products?
Competitors typically have some of these features in different “modules” that have to be purchased at an additional cost.
Is there on-premises as well as SaaS?
What industry frameworks does ConnectSecure support?
What category of the NIST framework does CS-VM operate within?
Integrations
What third-party products does CS-VM integrate with, and where can I get more information?
Does it integrate with SIEMs?
Where do you get your vulnerability feeds from?
Infosec
How does ConnectSecure ensure the security of its own product(s)? How can I be sure I am minimizing the chance of a supply chain attack on my client?
Principle of Least Privilege: Access to code and credentials is customized to meet and not exceed the needs of the employee.
Automated Tools to Monitor Internal Behaviors and Vulnerabilities: This was the Sprinto tool. We can examine how internal assets map to the standard for compliance of the asset, and we can also understand how our internal staff is behaving relative to their development privileges and assigned responsibilities.
Sophisticated Development Operations: Leveraging GitHub and Pipeline, the Dev/Staging/Master-Production environments feature limited access and clearly defined rules that enable code to move from one environment to the next. This protects the production code from projecting any code that hasn't been fully tested and examined for infosec best practices.
As a feature of the point above, non-authorized staff, like Support, have no access to any of the code and no privilege to move the code through its Dev-Staging-Production journey
All access credentials are encrypted during the development process. When code may be shared between developers, sensitive information is not exposed nor is it available outside of defined permissions.
The multi-tenant environment of the software has been designed to ensure that the data and credentials from one tenant (client of the MSP) is completely separated from the data and credentials of another.
What type of internal security program does CS have and can you provide me with documentation?
Trial
How much time do I have to use the Free Trial?
Are there any features/functions of the production product that are missing in the Free Trial?
Capacity
How large an IT environment can CS-VM effectively support?
I understand that CS-VM is multi-tenant. Are there any practical limitations to how many clients I can host on one platform?
Buying
How is CS priced?
How do I buy CS-VM?
Is CS-VM available through distribution?
Function
Does your external scan look at the OWASP Top 10 vulnerabilities?
Does CS look at Configuration compliance?
What Active Directory hygiene does CS identify?
What assets/systems can CS-VM patch?
How do I prioritize remediation of vulnerabilities?
Other
What privileges do I need to give agents and probes?
What if my EDR stops the CS process?
Reduce risk across your client base
ConnectSecure’s MSP-tailored platform transforms your most common cybersecurity risk and compliance policy challenges into revenue opportunities. Charge up your security practice with:
- Automated vulnerability remediation: Go beyond just finding vulnerabilities — automatically patch third-party applications your RMM might miss
- Always-on attack surface monitoring: Continuously scan external, WAN, and LAN environments to protect clients from emerging threats
- Compliance and audit readiness: Provide detailed IT asset hygiene reports required by compliance frameworks and auditors
- Complete IT asset discovery: Know every device and application in your clients’ networks
- Risk-based prospecting tools: Prove your value and earn trust by showing prospects their actual security gaps
- Deep cloud visibility: Leverage Google Workspace and M365 assessments as well as Web Application Scanning to identify misconfigurations and more (all included in Premium)
Start Your Free 14-Day Trial of ConnectSecure Premium Edition. No credit card required.
Bonus: We favor pay-as-you-go over long-term contracts.











