
Protect your clients and your bottom line with ConnectSecure
The automated vulnerability management and compliance platform built by MSPs for MSPs to seal their clients’ digital borders and power profitable growth.Protect your clients and your bottom line with ConnectSecure
The automated vulnerability management and compliance platform built by MSPs for MSPs to seal their clients’ digital borders and power profitable growth.
Certified for security, privacy, and reliability
ConnectSecure is trusted by thousands of MSPs to deliver secure, top-notch Vulnerability and Compliance Management to their customers.
Continuous, automated protection at an industry-best price

Vulnerability Management
Identify, prioritize, and remediate security risks with speed and precision. Our solution scans thousands of applications and patches over 550 of them—5-7x what competitors can do—while turning vulnerability insights into new business opportunities.
Compliance Management
Take control of compliance gaps that make your clients a target of both regulators and threat actors. With automated monitoring and remediation across major frameworks, you can swiftly capitalize on the growing demand for compliance services.
Premium Features
Gain unprecedented visibility into cloud productivity environments with automated configuration assessments. The uncovering of hidden vulnerabilities in Microsoft 365 and Google Workspace enables you to prevent costly breaches, elevating your status to indispensable security partner.Trusted by thousands of MSPs.













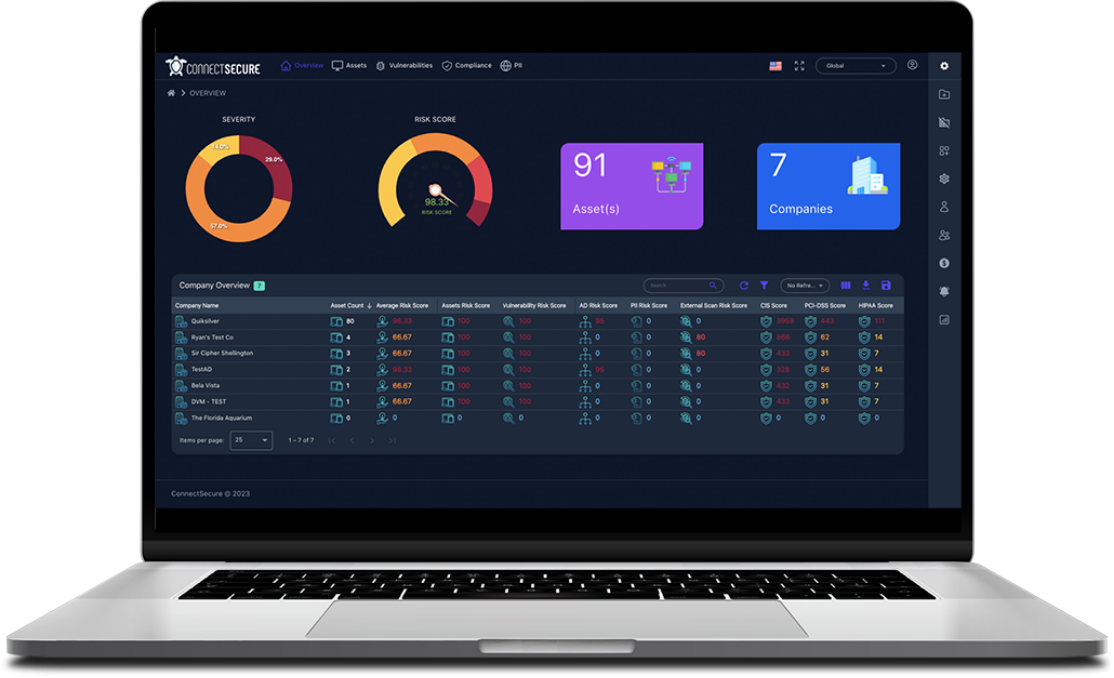
Don’t just identify risk—fix it
Effective security demands resolution. Our industry-leading patch coverage and intelligent prioritization efficiently secure client environments with minimal effort.
- Move beyond detection with automated vulnerability patching that saves MSP tech time
- Apply EPSS scoring to establish clear vulnerability priorities based on actual risk
- Provide comprehensive coverage for over 230,000 CVEs through daily NVD scanning and updates
- Deliver 5-7x better patch coverage than competitors across thousands of applications
- Gain comprehensive visibility with #1-rated CIS Controls and attack surface mapping

Open doors with comprehensive risk assessments
Compelling security insights pave the way for initiated client conversations. Equipped with risk scores and more, the case for your services writes itself.
- Showcase your security expertise with comprehensive assessments across hardware, software, and networks
- Win new business with assessment reports that highlight critical vulnerabilities and compliance gaps
- Help clients qualify for cyber insurance with thorough documentation of security controls
- Drive productive sales conversations with customizable reports that speak directly to client needs
- Identify hidden security threats that create immediate remediation opportunities
Get more from your team with automated, multi-tenant efficiency
Multi-tenant architecture brings ease of customer management from a single dashboard. No matter how many clients you add, efficiency rules.
- Manage your entire client base through one centralized interface for streamlined operations
- Automate recurring workflows to handle more customers with your existing team
- Deploy and configure policies across multiple clients simultaneously
- Receive consolidated alerts and notifications to quickly identify emerging threats
- Scale your MSP practice without complex infrastructure or additional headcount

Turn regulations into revenue engines
Your clients face ever-growing regulatory pressures—and we give you the ability to make sure they stay compliant and audit-ready. The result: a new revenue stream for your MSP.
- Support 16+ compliance frameworks including GDPR, HIPAA, PCI-DSS, and CIS
- Build recurring revenue through continuous compliance monitoring services
- Simplify regulatory adherence with automated compliance remediation
- Differentiate your practice with specialized compliance expertise and reporting
- Demonstrate compliance progress with before-and-after reporting that showcases your impact

Reporting that adapts to every client
Create and customize AI-powered reports that highlight your impact across all managed companies. ConnectSecure makes it easy to present progress and value in ways your clients instantly understand.
- Tailor content and layout for different audiences
- Build branded templates for repeatable reporting
- Generate AI summaries and recommendations fast
- Visualize improvement and ROI clearly
- Strengthen relationships with consistent communication
Start using ConnectSecure with a free trial!
Real results straight from our MSP community

Mitchell Matter
Co-founder | LockIT Technologies
Trent Gasser
IT Consultant | Palitto Consulting Services
Luis Alvarez
CEO | Alvarez Technology Group
Simon Hopkin
Head of Cyber Security | ITPStool for us to drive engagement. It’s very quick and easy to deploy and you get almost immediate results.”

Christophe Gagnon
Director | CyberVision 24/7
Karl Bickmore
CEO | Tech IT
Dennis Houseknecht
CTO | WatSec Cyber Risk Management
Tim Fournet
CISO | RaderTurn vulnerabilities into revenue. Watch the impact of ConnectSecure in action.
Cybersecurity Risk Analysis: What the Data Reveals About Your Exposure
Key Takeaways
Cybersecurity Assessment Checklist: How to Identify and Fix Your Biggest Blind Spots
Overview: A cybersecurity assessment identifies unmanaged assets, vulnerabilities, and control gaps...
How to Choose the Right Asset Discovery Tools for Your Organization
Unmanaged assets are one of the most persistent weaknesses in cybersecurity. They appear without...

Learn how to win business with cybersecurity vulnerability assessments
Cyberattacks present an existential threat to SMBs. But you can help them thrive. Earn their confidence and build your credibility by leveraging cybersecurity assessments. It’ll be good for your bottom line.